Access Control in Database Management Systems
Daniel Cvrček
Department of Computer Science and Engineering, TU Brno
Božetěchova 2, Brno 612 66
e-mail: cvrcek@dcse.fee.vutbr.cz
Abstract. Stormy expansion of IT in recent years
lead to the information systems spread into various public and private
organizations. So database management systems (DBMS) arised in 70-s. Those
systems have been able to ensure effective access to stored information.
Very soon, however, they became inadequate. Distributed DBMS has been introduced
with development of distributed computing. Those have been able to exploit
new capabilities of computer nets. Everything looked just fine, but in
that time first large information leaks appeared from large DBMSs. And
so new conception appeared - data security. Database damage has
not affected one user but information system of a whole organization and
impacts have become unpredictable but surely very important. Development
has not stopped and data has become available for various types of users.
This fact has lead to another sharpening of security problems. First attempts
for secure DBMS appeared. Today, we are using various techniques to secure
data. Logical access control is one of necessary conditions for providing
secure system. Talking about access control, there were two variants for
a long time - mandatory and discretionary. New approaches appeared with
recent post-relational DBMSs.
Abstrakt. Rychlý vývoj IT v minulých letech vedl ke
vzniku databázových systémů (DBMS). Ovšem původní systémy velmi brzy nedostačovaly
potřebám. S vývojem distribuovaného zpracování vznikly distribuované databázové
systémy, které umožnily využít nových možností počítačových sítí. Všechno
vypadalo v pořádku, ale najednou začalo docházet k “únikům informací” z
rozsáhlých DB systémů - na řadu přišel nový pojem bezpečnost dat.
Poškození databáze už neovlivnilo jednoho člověka, ale informační systém
celého podniku a dopady se staly nepředvídatelnými, ale zcela jistě významnými.
V této době vznikly první pokusy o vytvoření bezpečných DBMS. V současné
době používáme rozmanité techniky pro zajištění bezpečnosti dat. Ukazuje
se ovšem, že logické řízení přístupu k datům je jednou z nutných podmínek
pro vytvoření bezpečného systému. Přístupy k této oblasti se postupem doby
vyvíjely. Dlouhou dobu existovaly dva základní - povinné a nepovinné řízení
přístupu. V poslední době, spolu s rozvojem postrelačních DBMS, se objevily
nové principy pro logické řízení přístupu.
1. Introduction
Result of the database management systems use is existence of one data
set on which are working all users and applications in an organization.
On one side, hardly solved problems with duplication, inconsistency and
application dependency of data disappear. On the other side much more dangerous
security problems appear. There is a brief introduction to them on next
lines.
Design of secure DBMS assumes identification of security risks and selection
of right security policies (what is the security system supposed
to do) and mechanisms (the way we are going to achieve that) for
their neutralization.
Secure database system should satisfy three basic requirements on data
protection: security, integrity and availability.
What is the content of those words?
-
Ensuring security - preventing, detecting and deterring improper
disclosure of information. This is especially important in strongly protected
environments (e.g. army).
-
Ensuring integrity - preventing, detecting and deterring
improper changes of information. The proper function of any organization
depends on proper operations on proper data.
-
Ensuring system availability - effort for prevention of improper
denial of service that DBMS provides.
1.1. Security Policies
Security policies are guidelines describing all (if possible) actions pertinent
to the information system. Logical access control belongs to that area
and so security policies should define principles on which is design of
secure DBMS based.
Generally, policies should give answers on basic security questions.
Policies can be divided into two basic types - of minimal (army) and maximal
(university) privilege. System with such a policy is called closed or opened,
respectively.
Talking about access control, the way of administration of access rules
should be determined.
-
hierarchical decentralized - central authorizer distributes
responsibilities among dependent subauthorizers
-
ownership based - owner of an object (its author) determines
access to the object
-
cooperative authorization - authorization of special rights
for special resources is approved by all members of predefined group
1.2. Security Mechanisms
In the moment when politics are defined, mechanisms that fulfill them can
be selected. Mechanisms are external:
-
administrative controls
-
physical controls
and internal that are part of information system itself:
-
authentication - user identity is verified; this process is based
on knowledge of something, ownership of an object or on physical characteristics
of user
-
authorization - system answers only those queries that user is authorized
for (access control)
-
audit - is composed from two phases; logging of actions in the system
and reporting of logged information
1.3. Security Threat
This word has been used several times already. Security threat is any hostile
agent which randomly or with use of specialized techniques can obtain or
change information in the information system. Random security threats are:
-
natural or accidental disasters- earthquake, water damage
or fire. As data as hardware is damaged which leads to the integrity violence
and service rejection.
-
errors and bugs in hardware andsoftware - causes improper
application of security policies.
-
human errors - unintentional violations such as incorrect
input or wrong use of applications.
Intended security threats can be categorized according to their originator:
-
authorized users - abuse there privileges
-
hostile agents - various hostile programs - viruses, Trojan
horses, back-doors
1.4. Requirements on DBMS Security
At this moment we have basic image of information system security and we
can take a look at concrete aspects that should be covered with DBMS security
mechanisms.
-
Protection from improper access- only authorized users should
be granted access to objects of DBMS. This control should be applied on
smaller objects (record, attribute, value).
-
Protection from inference - inference of confidential information
from available data should be avoided. This regards mainly statistical
DBMSs.
-
Database integrity - partially is ensured with system controls
of DBMS (atomic transactions) and various back-up and recovery procedures
and partially with security procedures.
-
Operational data integrity - logical consistence of data
during concurrent transactions (concurrency manager), serializability and
isolation of transactions (locking techniques).
-
Semantic data integrity - ensuring that attribute values
are in allowed ranges. This is ensured with integrity constraints.
-
Accountability and auditing - there should be possibility
to log all data accesses.
-
User authentication - there should be unambiguous identification
of each DBMS user. This is basis for all authorization mechanisms.
-
Management and protection of sensitive data - access should
be granted only to narrow round of users.
-
Multilevel security - data may be classified according to
their sensitivity. Access granting should then depend on that classification.
-
Confinement (subject isolation) - there is necessity to isolate
subjects to avoid uncontrolled data flow between programs (memory channels,
covert channels).
At least five aspects from the previous list must be ensured with special
techniques that do not exist in unsecure DBMSs. There are three basic ways
to do it:
-
flow control - we control information flows in frame of DBMS
-
inference control - control of dependencies among data
-
access control - access to the information in DBMS is restricted
Cryptographic techniques can be added to the controls.
1.4.1. Flow Control
Flow control regulates distribution (flow) of information among available
objects. E.g. reading of information from object X and its direct writing
into object Y.
Flow control policies need list of acceptable information flows and
their constrains. Flow constraints are often based on classification of
system elements and definition of acceptable flows between classification
levels.
1.4.2. Inference Control
The aim of the inference control is to avoid indirect disclosure of information
(set of data X that can be read by user can be used for determination of
data set Y (Y=f(X)) ). Generally there are three ways to unauthorized data
disclosure:
-
correlated data - typical channel when visible data X are
semantically related with invisible data Y
-
missing data - result of query contains NULL values that
mask sensitive data. Existence of that data may by detected that way.
-
statistical inference - typical for databases that provide
statistical information about entities.
Statistical databases do not allow direct access to data and user has to
query only statistical data. Attacks in this DBMSs can be faced with two
different approaches:
-
data perturbation - concrete data are replaced with statistical
results
-
query controls - more frequently used, mostly it is based
on minimal and maximal number of items that are concerned with query. Results
are satisfactory but this technique is expensive and difficult for administration.
1.4.3. Access Control
Access control is responsible for control of rules determined by security
policies for all direct accesses to the system. Traditional control systems
work with notions subject, object and operation.
For better image look at the figure of secure DBMS.
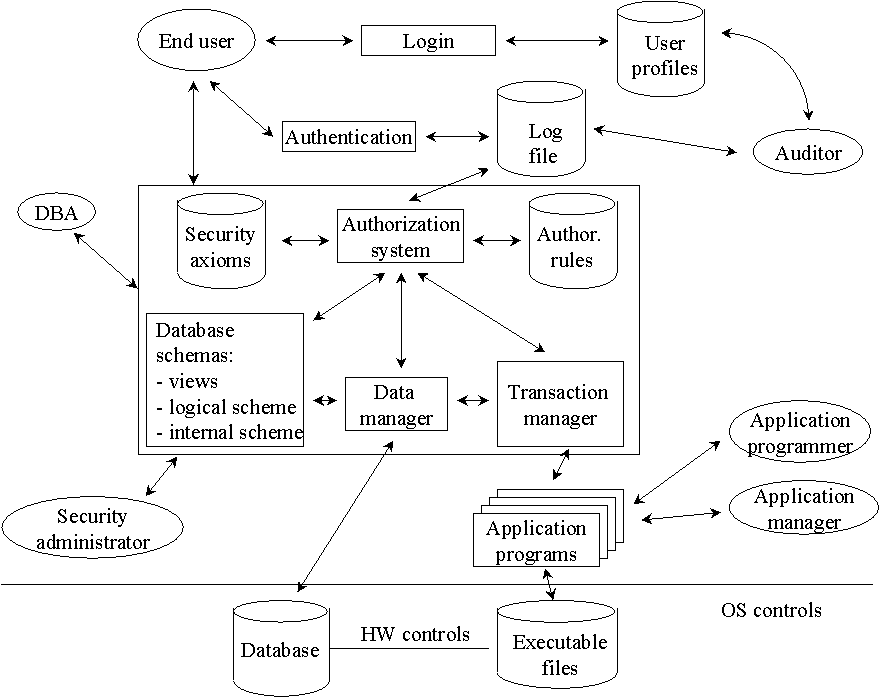
Fig.1 Schema of secure database management system
2. Security Models
The aim of security modeling is to create abstract, software independent,
conceptual model from requirements specification for system protection.
Security model should provide rich semantic representation which allows
description of functional and structural properties of security system.
It should also provide definitions for protection requirements and system
policies. The proof of model properties should be available, too.
It is clear that level on which we decide to describe access control
can greatly differ as we will see in the next paragraph. Description of
basic approaches for access control is introduced in chapter 2.2. Description
of concrete models follows.
2.1. Abstractions of Access Models
Access control models can be classified in several levels as proposed by
LaPadula and Williams. Following levels proceed from general to more implementation
dependent:
-
trust objectives - definition of basic requirements on the
system trustfulness
-
requirements on external interface - security requirements
on interface system-environments
-
internal requirements - requirements that must be satisfied
in system components
-
operational rules - describe assurance of internal requirements
-
functional design - functional description of behavior of
system components
Models that are going to be described are on level 3. TBAC and RBAC model
families partly interfere with level 2 because they are much more general
and cover wider range of problems.
2.2 Types of Access Control Models
Security models can be classified according to many aspects. For example
target system, type of security policy, addressed security aspects, type
of control (direct or of flows) and so on. In the moment we will talk about
type of security policy that is enforced by the model.
Two basic model types arised very soon - discretionary and mandatory
access control. Owner of data governs access in the former one. This is
the most common form of authorization administration - ownership based.
That policy is very flexible but also very difficult for control from the
global point of view. Models with mandatory access control enforce global
policy by the flow control among security levels that are assigned to objects.
It seemed that nothing else would exist but OO technologies have encourage
new approaches that reflect OO DBMSs and new requirements of commercial
sphere. The first one is RBAC - access control based on roles and the second
one is TBAC which is based on concept of task. TBAC brings absolutely new
ideas and notion of active security.
We finish this introduction and try to describe policy types on concrete
models.
2.3. HRU - Matrix Access Model
The HRU (Harrison-Ruzzo-Ullman) model covers security of data for DBMS
and OS. It was proposed in 1971 and in 1976 was formalized.
2.3.1 Authorization State
Authorization state is derived from relations between objects and subjects.
It is defined as triple Q=(S, O, A) where S is set of subjects, O is set
of objects (contains also subjects) and A is access matrix (A[s, o]=r).
Authorization state for DBMS can be enriched by predicates of access
rights. Those predicates may by data, time, context or history dependent.
Six primitive operations are defined for authorization state administration.
They are granting and revoking of rights r from A[s, o], creating
and deleting of subject s, creating and deleting of object o.
Operations are used for composition of commands for authorization state
modifications. Harrison assumes that modification commands have two parts;
conditional and executive. The executive part is performed when the conditional
is true.
Set of possible access rights depends on object. The model knows read,
write,
append, execute,
own. The last one determines owner
that administers access to it.
2.3.2 Administration of Authorizations
The owner of object may grant/revoke any rights (except own) to the given
object for other subjects. Even those rights that he does not possess in
the moment. This approach breaks principle of attenuation of privileges.
There are modifications of access rights in some systems that allow
other subjects to administer access rights. This is expressed by explicit
flag on access right that may have two forms.
-
copy flag - m* in A[s1, o] allows grant
an access right m for object o to other subjects, rights
of subject
s1 do not change and subject s2
receives right m for object o
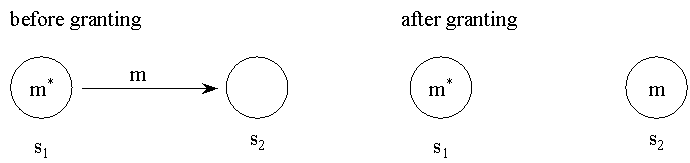
Fig. 2. Use of copy flag
-
transfer flag - subject
s1 grants right
m
for object
o to subject
s2, subject s1
loses the right. Subject
s1 has got m+
(with transfer flag)
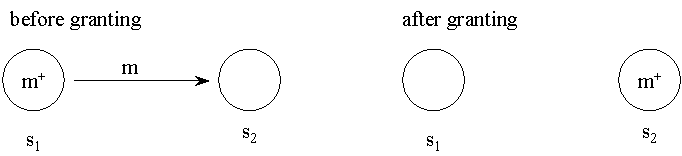
Fig. 3. Use of transfer flag
2.3.3 Model Extensions
The HRU model is very flexible for expression and control of access rights
for information. The most important problem is security question
(Is there a reachable state to the given starting authorization state where
a subject receives certain right for given object?) that is undecidable.
This problem coheres with danger of Trojan horses in DAC.
The model has been extended several ways for security question decidability.
-
Schematic protections model (Sandhu)
-
Extended schematic protection model (Ammann and Sandhu)
-
Typed access matrix (TAM) model (Sandhu) - each object and subject
has a type that is assign with creation of entity and it does not change
during lifecycle.
2.4. Bell-LaPadula Model
This model is extension of HRU model oriented on definition of security
requirements in complex systems where system elements can be classified
(security levels). The model was proposed in 1973 for operation systems.
The model became referential for mandatory access control (MAC).
2.4.1 Classification of System Elements
The BLP model is based on classification of system elements that is expressed
with security levels. Each security level has got two parts: classification
and set of categories.
The classification is fully ordered set of four elements - {TS, S, C,
U} (from the biggest). The set of categories is a subset of non-hierarchical
set of elements that corresponds to application area and environment. The
security levels with operation ? compose lattice
that is defined by the following way:
L1=(C1, S1) ?
L2=(C2, S2) ?
C1 ? C2 ?
S1 ?
S2
Each user has got clearance and may work in the system on any level
that is dominated (lower or equal) by clearance. Each object receives security
level during its creation.
There are four access rights: read-only, append (can not see existing
content), execute and read-write.
2.4.2. System State
System state is described with tuple (b, M, f, H) where:
-
b - actual access set - set of triples <subject, object, access right>
-
M - access matrix which describes subjects’ access rights to objects (see.
HRU model)
-
f - level function that associates security level with every object and
subject in the system f: O? S®
L each object has got security level fo each subject has got
two security levels, one is security clearance (fs) and the
second is actual security level on which the subject actually works (fc)
-
H - actual object hierarchy - oriented rooted tree that nodes represent
objects in the system; there are no unavailable objects (compatibility
property - security level of son dominates security level of its father)
The system state changes with execution of operations gain/free
access (starting and finishing of access), grant/revoke access right,
create/destroy
object, change subject’s security level and finally change
object’s security level.
2.4.3. Axioms
The most important thing the model introduces is reference monitor
and system of properties that validity is checked by the reference monitor.
Simple security (ss) property
Trusted subject can read or write an object just when its security clearance
dominates security level of the object. System state v=(b, M, f, H) satisfies
ss-property when each element of M[s, o] that keeps read or write access
right satisfies fs(s) ? fo(o).
Star (*) property
Any subject may keep access right append on object when security
level of the object dominates actual security level of subject. This subject
may write the object just when level of object equals to level of
security subject and subject may read the object when object’s security
level is dominated by subject’s security level. The formal notation is
as follows:
Let s Î S, SÍ
S, where S is set of untrusted subjects; then
append Î M[s, o] ?
fc(s) ? fo(o)
write Î M[s, o] ?
fc(s) = fo(o)
read Î M[s, o] ?
fc(s) ? fo(o)
Note: Those relations imply two properties that are often used.
No read-up - I can read just objects that security level is dominated
by my security level.
No write-down - I can write just objects that security level
dominates my security level.
Discretionary security property (ds-property)
Each actual access must be in the access matrix. Subject may perform
only those accesses that he has got access rights for. The system state
guarantees the ds-property just when the following equation holds for all
subjects, objects and access rights:
<s, o, m> Î b ?
m Î M[s, o]
3. Conventional models for OO DBMS
With appearance of object oriented DBMSs arised need for new security models
that would exploit new properties of OO technology. It is natural that
first such models used principles that had been examined through years
of practice in relational database systems.
Models have been accommodated by new definitions of objects, subjects
and access rights and have employed some features of OO data models - inheritance,
composite objects. Strong influence of relational data model however stayed.
Above all, the access matrix that is ideal for relation data model but
it has got nothing to do ”with objects” in my opinion. The ORION model
belongs to that category. Next paragraphs introduce models that exploit
other important features of OO data model - messaging and encapsulation.
3.1. Authorization model ORION
This model was introduced by Rabitti in 1991. It enforces discretionary
access control and takes in mind some characteristics of OO systems - inheritance,
composite objects and versioned objects.
3.1.1. System Elements
Subjects are groups of users (roles) into that are users added according
to the position in organization. User can have more than one role. Roles
compose lattice with operation implication (defined on basis of relations
between sets of access rights). There is superuser on the top of the lattice
and on the bottom is user (these notions may be only abstract but are necessary
for complete lattice).
Objects are databases, classes in databases, instances of classes and
their components and also sets of instances of a given class or sets of
attributes. Objects compose a lattice (system, databases, classes, ...).
3.1.2. Access Rights
There are defined five access rights:
write,
write_any
(allows
object to be written), read,
generate and read_definition.
Access rights again compose a lattice from that are derived implicit access
rights (operation ® ). Access rights are arranged
into three groups:
A.up - rights are propagated from low objects upto high ones, A.up={WA,
RD}
A.down - rights are propagated from high objects to low ones, A.down={W,
R}
A.nill - access rights that are not propagated, A.nil={G}
Access rights are specified by users. Because there are no administration
rights, the access right implies administration of itself.
The system automatically derives implicit authorizations from the explicit
ones with use of relations among subjects, objects and access rights. Access
rights can be positive/negative and strong/weak. The latter classification
divides authorizations into two sets.
Strong authorization base (AB)
There is defined function i: S x O x A ®
(True, False, Undecided), over the set. This function does not have to
decide the access granting. Two properties must stay true:
-
consistency property AB
if $ (s, o, a): (s, o, a) ®
(s1, o1, a1) ?
$
! (s2, o2, a2): (s2, o2,
a2)
® (s1, o1,
a1)
-
nonredundancy property AB
if $ (s, o, a): (s, o, a) ®
(s1, o1, a1) ?
(s1, o1, a1) ?
AB
Weak authorization base (WAB)
Access rights from this set may be overwritten with strong ones or
more specific weak rights. There is defined function d: S x O x A ®
(True, False) that decides access granting with the final force.
-
completeness property WAB
for " [s, o, a] $
[s1, o1, a1] Î
WAB: [s1, o1, a1]®
[s, o, a]
-
consistency property WAB
for " [s, o, a], if $
[s1, o1, a1] Î
WAB: [s, o, a] ® [s1, o1,
a1] ?
$ ! [s2, o2, a2]
Î
WAB: [s2, o2, a2]®
[s1, o1, ? a1]
There is another property between strong and weak authorization bases.
coexistence property of AB and WAB
for " [s, o, a] Î
WAB must not $ (s1, o1,
a1) Î AB: [s1, o1,
a1]® [s, o, ?
a]
3.2 Message Filter Model
Jajodia and Kogan have proposed a variant of reference monitor from the
BLP model for OO data models - message filter. This model exploits data
encapsulation and messaging (it is the only one way of information exchange).
The control of data flow is done by control of messages in the system.
3.2.1 Entities
All entities in the OO system are objects that contain information and
that process actions. Each object obtains security level L(o) during creation.
This level does not change. For proper function of the system, following
conditions must be fulfilled:
-
L(o) ? L(c), o is object of the class
c
-
L(cs) ? L(cp), cs
is subclass of the class cp
The model assumes that all objects are single-level (all components have
the same security level). This requirement is common for more security
models and it gave birth to special methodologies for transformation of
multi-level objects.
Special object type is user session, which represents a user.
This object may, in contrast to other objects, execute methods from its
own initiative.
3.2.2 Information Flow
There defined two basic types of data flows in the system: message sending
and
object creation. Receiving of a message is not data flow itself
until data items of the receiver are not changed.
All messages can be decomposed down to three primitive messages that
are sent by object to itself. They are
read (g=(READ, (ai),
r)), write (g=(WRITE, (aj, vj), r))
and create (g=(CREATE, ((v1, ..., vk),
Sj), r)).
3.2.3 Algorithm of Message Filtering
All messages are controlled in the
message filter that mediates
all messages in the system. The message filter associates security level
rlevel
to the message (it is the highest L(o) of objects that the message has
gone through).
This criterion is used for the filtering according to the following
description:
1. non-primitive message, o1®
o2
a) L(o1)=L(o2), message and answer are not restricted
b) L(o1)<>L(o2), message is blocked and answer
is forced empty
c) L(o1)<L(o2), message is sent further and
answer is forced empty
d) L(o1)>L(o2), message and answer are not restricted
2. primitive message of object o to itself
a) READ - without restriction
b) WRITE - execute only if rlevel = L(o)
c) CREATE - rlevel must be dominated by the security level of
the new object
4. Role-Based Access Control
This model family has been proposed to satisfy requirements of the commercial
sphere. The basic idea is notion of role. Users are granted roles that
allow them to perform certain actions that are assigned to the roles. Roles
are usually created according to the functions in organization. In the
moment we decide to revoke or change access from a user, the only one thing
we have to do is remove him from a group or reassign him to another one.
This change is very easy for an administrator.
This approach offers very suitable abstraction for expression of security
policies of large companies and seems to be promising alternative to the
traditional MAC and DAC models. RBAC is suitable for environments where
MAC models are too strict. It has been proofed that RBAC can simulate mandatory
access models and, in addition, that MAC models are specific case of RBAC.
One may say that RBAC is based on something that is very similar to
groups that are used in many older models. Groups of users are used to
associate subjects with the same access rights. Such a group does not represent
a role but common needs for execution of certain system actions. Roles
in RBAC exploit groups to abstract access rights needed for some concrete
actions that are later accessible for role members.
Narrow, specific meaning of roles can not exhaustively express status
of users. It seems that for effective implementation of role-base access
control we need to define three aspects. They are role,
individuality
and locality. I demonstrate it on an example when a firm engages
a new person - Smith. His position is seller (it is his role). During the
trial period you do not want him to do transactions with banks (individuality)
and finally you do not want him to access your system elsewhere than in
New York (locality).
What are the advantages of the system? You are not bound during the
policy selection, model offers strict separation of duties, ease expression
of organizational policy and of course easy access rights administration.
5. Task-Based Authorization Control (TBAC)
TBAC models, in contrast to classical relationship subject-object-access
right, use new one oriented on tasks. Granting of access control is
component of various phases of task execution with abidance of application
logic. TBAC models compose basis for active security models that
are needed for distributed computing and workflow management. These models
approach the access rights administration from the view of task activity
and offer abstractions and mechanisms for authorizations administration
at run-time.
Disadvantages of all other models from the view of TBAC are centralistic
oriented (central common resources), access rights are very primitive and
without relation to actual system state. Also there are no records about
use of access rights.
Clearance is expressed as signature of a form in the real world. The
given person undertakes responsibility for actions that are allowed with
the signature. All relevant actions are automatically disabled after the
signature expirates. The aim of TBAC models is to decrease demands of administration
in large and complex systems and shift this administration to the described
idea.
New notion - authorization step has been introduced for this
purpose. It is analogy of a form. Creation of the authorization step means
change of system authorization state (a given subjects is granted access
rights) for the given time and for the given authorization step. Authorization
state can be expressed with the following equation:
P Í S x O x A x U x AS
Beyond subjects (S), objects
(O) and access rights (A)
there are number of use (U) and authorization step (AS).
Each authorization step has got its own authorization state. The initial
state contains set of access rights of maximal size. This size is decreasing
during lifetime of the authorization state.
Because authorization steps are not in the system isolated there are
defined relations that can be used for expression of security policy.
A1state1 ® A2state2
if A1 goes to state1, A2 must go to state2
A1state1 < A2state2
if A1 goes to state1 and A2 go to state2 then A1
must do it first
A1state1 # A2state2 if
A1 is in state1 then A2 must not be in state2 and
vice versa
A1state1 ||| A2state2 A1
must be in state1 if A2 is in state2
Note: A1, A2 are authorization steps and state1
and state2 are states of steps A1, A2.
6 References
[1] Castalo S., Fugini M.G., Martella G., Samarati
P.:, Database security. Addison-Wesley & ACM Press, 1995
[2] Thomas R.K., Sandhu R.S.: Task-based Authorization
Controls: A Family of Models for Active and Enterprise-oriented Authorization
Management, Chapman & Hall, 1997
[3] Ferraiolo D.F., Cugini J.A., Kuhn R.D.: Role-Based
Access Control: Features and Motivations. Proceedings of the 11th Annual
Computer Security Applications Conference (CSAC '95), 1995
[4] Olivier M.S., Von Solms S.H.:, A Taxonomy for
Secure Object-Oriented Databases, ACM Transactions on Database Systems,
pgs. 3-46, March 1994
[5] Hilchenbach Burkhard: Observations on the Real-world
implementation of Role-based Access Control, 20th National
Information Systems Security Conference, 1997



