ASNM-NPBO Dataset
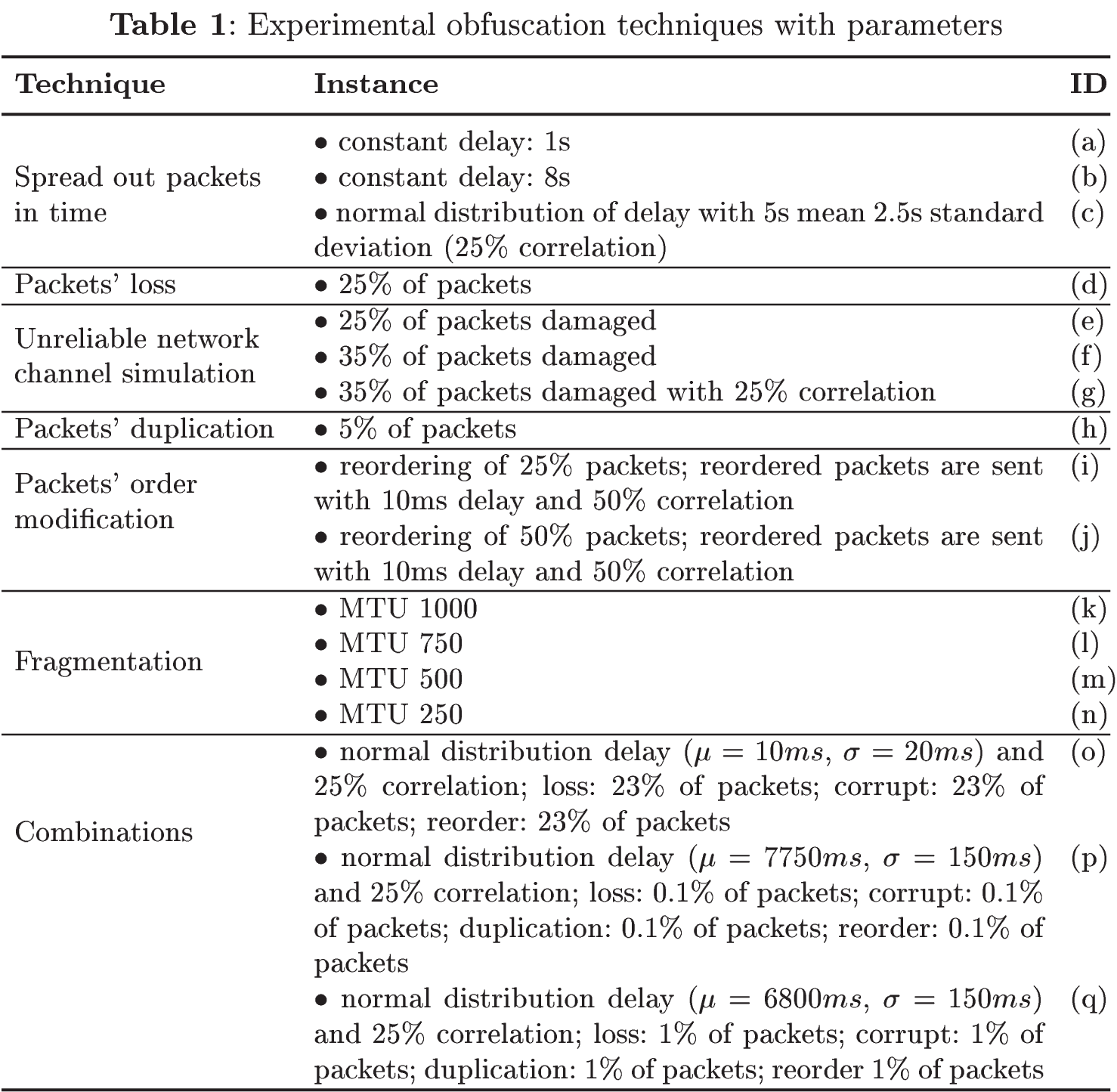
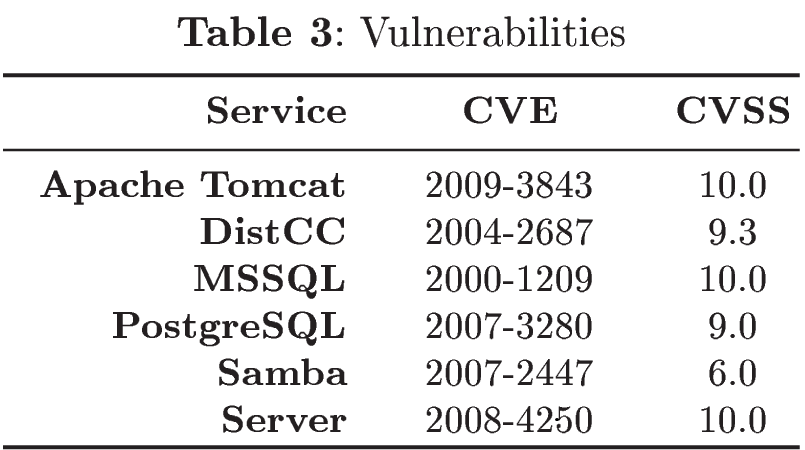
The ASNM-NPBO dataset (Advanced Security Network Metrics & Non-Payload-Based Obfuscations) consists of ASNM features [1, 2] extracted from tcpdump capture of obfuscated malicious and legitimate TCP communications on selected vulnerable network services (Table 3). The selection of vulnerable
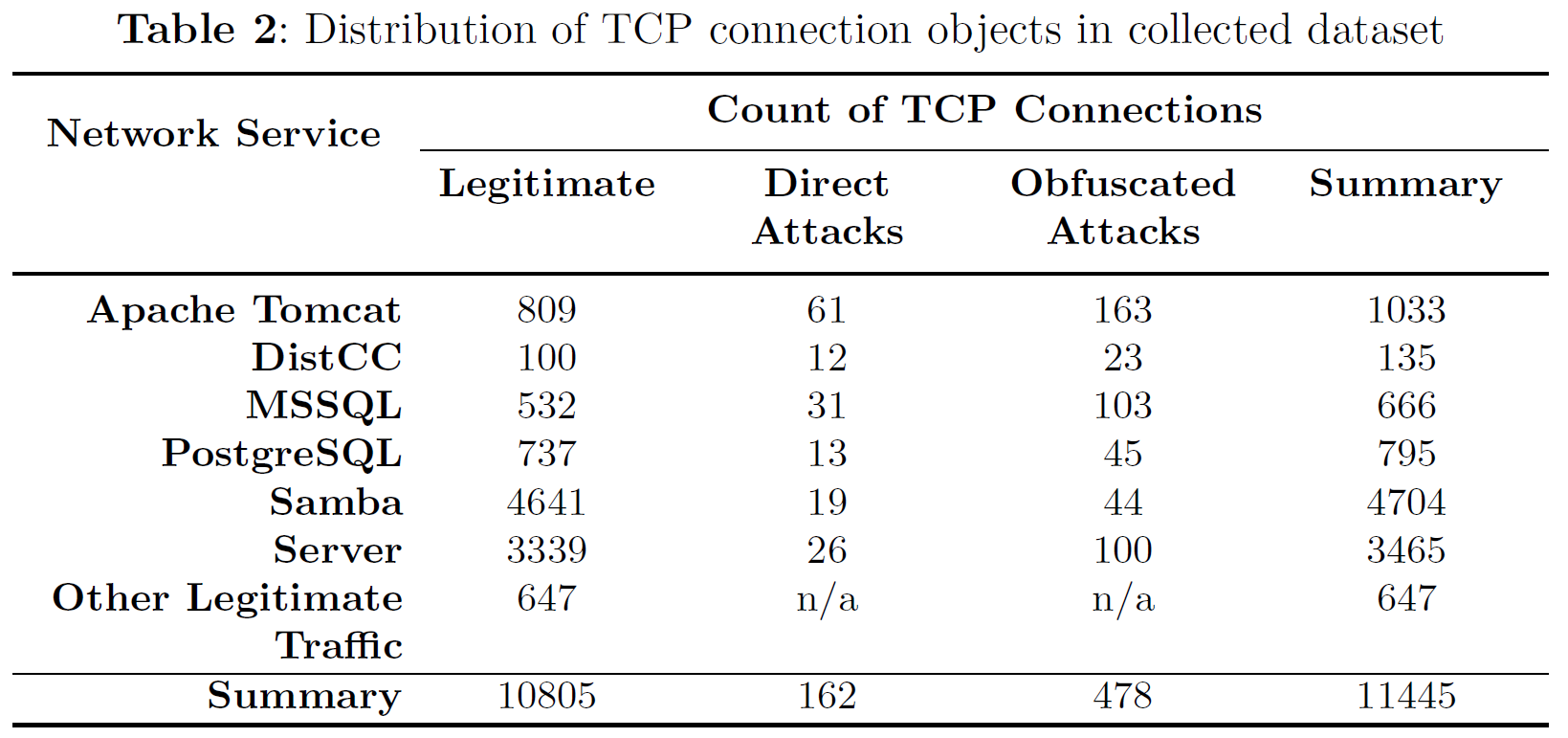
services was aimed on high severity of their successful exploitation leading to remote shell code execution through established backdoor communication. We employed several non-payload-based obfuscation techniques (Table 1) when exploiting vulnerable services in virtual network conditions, while legitimate representatives of the dataset were collected from two sources. The first source represented legitimate traffic simulation in our virtual network architecture and also employed non-payload-based obfuscations for the purpose of real network simulation. As the second source, common usage of all selected services was captured in campus network, and all traffic was anonymized and further filtered on high severity alerts by signature based NIDS Suricata and Snort through Virus Total API. Note that SNORT was equipped with Sourcefire VRT ruleset and SURICATA utilized Emerging Threats ETPro ruleset. The final composition of the dataset is depicted in Table 2.
Labeling
The ASNM-NPBO dataset contains 4 types of labels which are enumerated by increasing order of their granularities in the following listing:
The two-class label, denoted as label_2, says whether an actual record represents network attack or not.
The three-class label, denoted as label_3, distinguishes among legitimate traffic (symbol 3), direct and obfuscated network attacks (symbols 1 and 2).
The third label, denoted as label_poly, is composed of 2 parts: a) three-class label, and b) acronym of network service. The label represents type of communication on particular network service.
The last label, denoted as label_poly_o, is composed of 3 parts: a) three-class label, b) employed obfuscation technique, and c) acronym of network service. The label has almost the same interpretation as the previous one, but moreover introduces employed obfuscation technique (identified by ID from Table 1) into all obfuscated attack instances.
Introducing Paper
ASNM-NPBO dataset was introduced in the paper [3], which is an extension of original ideas presented in dissertation thesis [2].
Download
ASNM-NPBO dataset in CSV format can be downloaded [here].
References
-
HOMOLIAK Ivan, BARABAS Maros, CHMELAR Petr, DROZD Michal a HANACEK Petr.: ASNM: Advanced Security Network Metrics for Attack Vector Description. In: Proceedings of the 2013 International Conference on Security & Management. Las Vegas: Computer Science Research, Education, and Applications Press, 2013, s. 350-358. ISBN 1-60132-259-3. Download link.
-
HOMOLIAK Ivan.: Intrusion Detection in Network Traffic. Dissertation thesis, University of Technology Brno, Faculty of Information Technology, 2016. Download link.
-
Ivan HOMOLIAK, Martin TEKNOS, Martin OCHOA, Dominik BREITENBACHER, Saeid HOSSEINI, Petr HANACEK: Improving Network Intrusion Detection Classifiers by Non-payload-Based Exploit-Independent Obfuscations: An Adversarial Approach, EAI Endorsed Transactions on Security and Safety, Volume 5 (Number 17), 2019. Download link.

